This is how we deal with Spam, Impersonation & Phishing (they):
- Externally, deploy eyes and ears to see and hear where they usually congregate. They also infiltrate our midst from time to time.
- Internally, we have intelligent workers (system bots) on duty monitoring for these fraudulent accounts or visitors every second.
- Users will be allowed to report anything out of place. We'll also have them assist us in identifying and reporting offenders. Guess we could call it a kampong spirit for helping keep unwanted visitors or something far worse from entering our kampong.
Their usual hang-around.
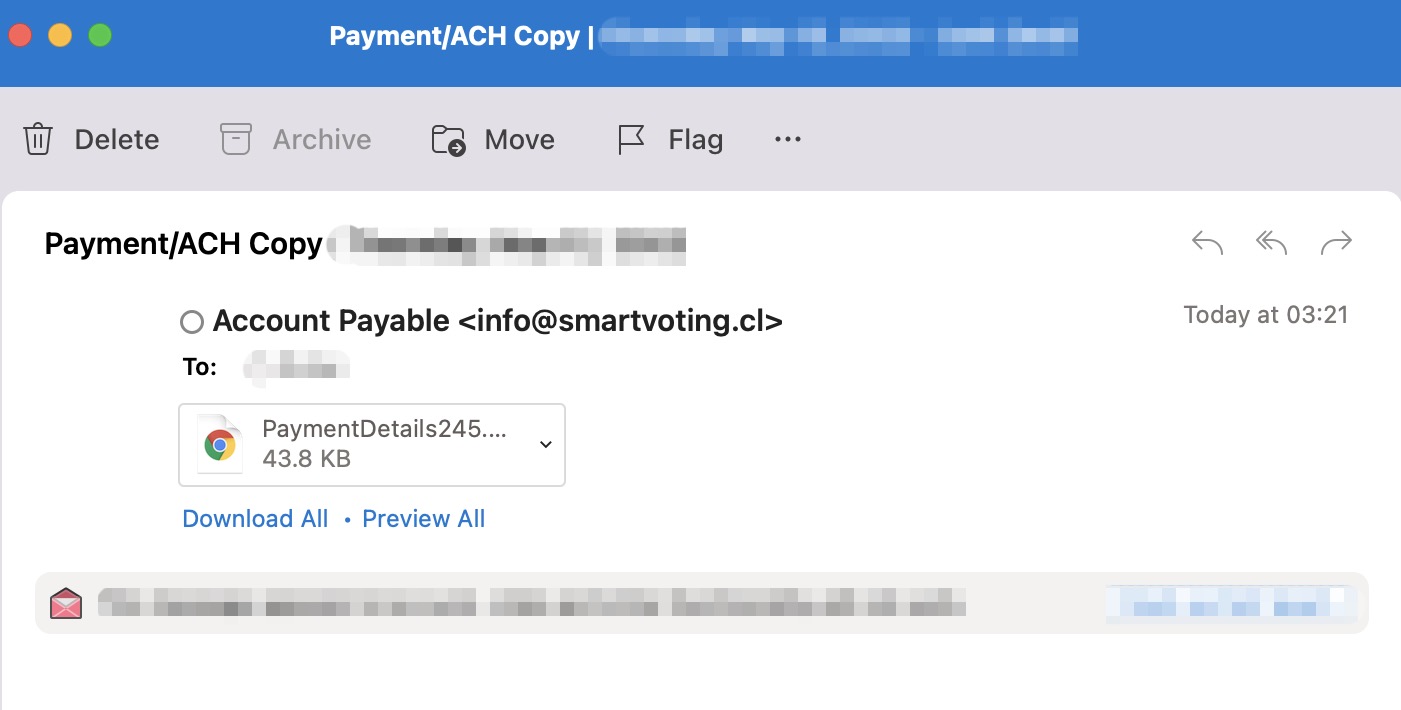
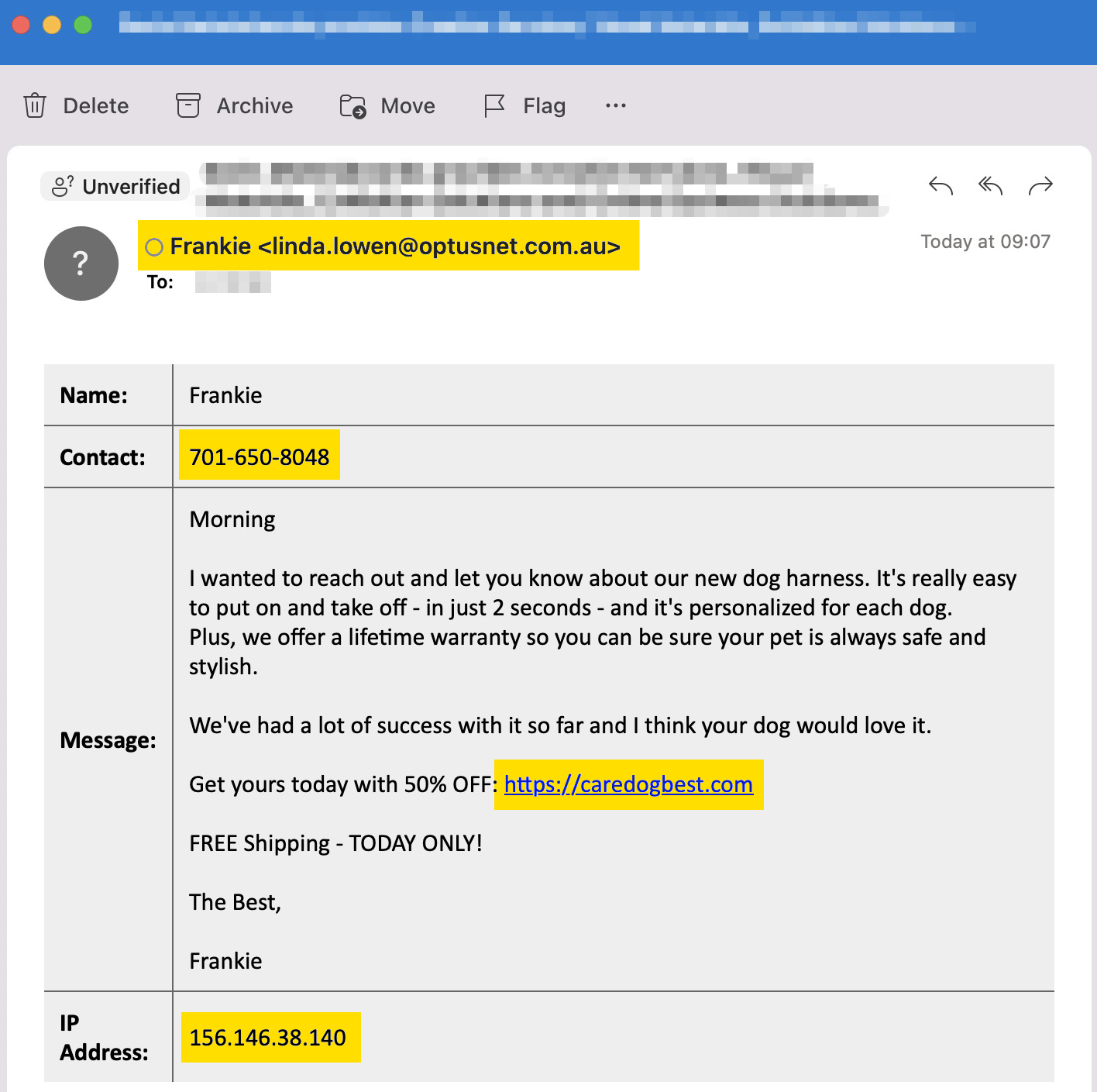
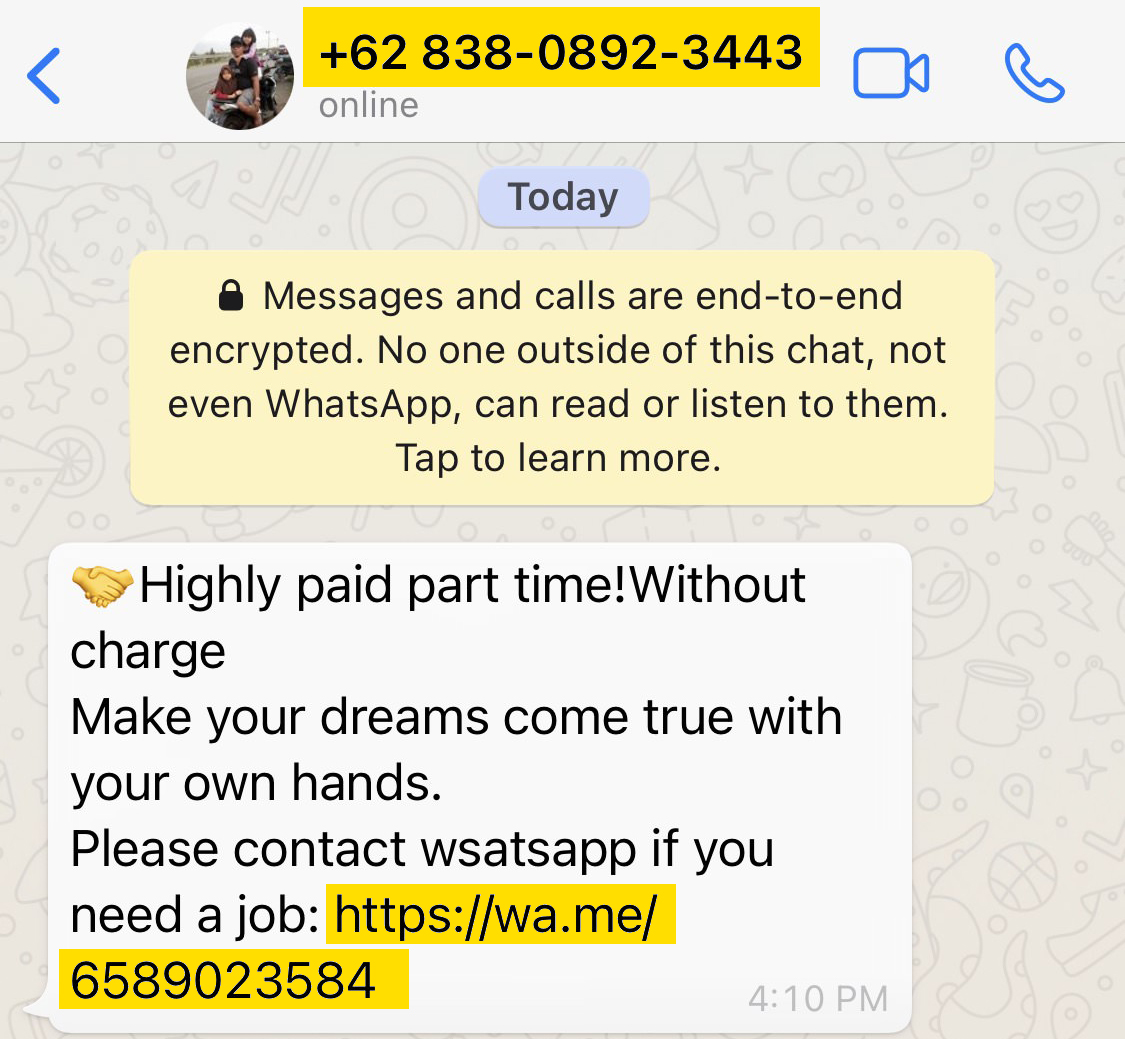
Most are primarily trained programmers using tools like temporary email, numbers, web hosts, connections and locations. So we know where to place our eyes on them.
These are already available in s͛Card.
- We have a system that checks and creates profiles and logs in registered dubious activists. We use tools like SI Blacklist & Google Web Risk.
- Shortlinks can reduce the number of characters for long domains that use rel=, ref=, and many tracking tokens. However, we often don't know if a shortlink is malicious. s͛Card checks links for safety concerns before displaying them on a user profile. This way, we can keep everyone who uses s͛Card safe from harm.